Establishing connection
Antavo’s single sign-on (SSO) solution is implemented through communication between three different servers.
Firstly, the connection between the identity provider (IdP) and the Keycloak server needs to be established. Your IdP stores user’s login data, and the SAML 2.0 / OIDC protocol is used to connect this information with the Keycloak server.
The following table defines the attributes that are configurable during the integration of SSO.
Config Name | Required | Should be filled out by | Description |
|---|---|---|---|
Service Provider Entity ID |
| User | The SAML Entity ID that the remote Identity Provider (IdP) uses to identify requests from this Service Provider. By default, this setting is set to the realms base URL |
Single Sign-On Service URL |
| User | The SAML endpoint that starts the authentication process. If your SAML IdP publishes an IDP entity descriptor, the value of this field is specified there. |
Single Logout Service URL |
| User | The SAML logout endpoint. If your SAML IdP publishes an IdP entity descriptor, the value of this field is specified there. |
Backchannel Logout |
| Antavo/User | The SAML logout endpoint. If your SAML IDP publishes an IDP entity descriptor, the value of this field is specified there. |
Backchannel Logout |
| User | Toggle this switch to ON if your SAML IDP supports back channel logout. |
NameID Policy Format |
| User | The URI reference corresponds to a name identifier format. By default, Keycloak sets it to |
Principal Type |
| User | This attribute specifies which part of the SAML assertion will be used to identify and track external user identities. It can be either Subject NameID or SAML attribute (either by name or by friendly name). Subject NameID value can not be set together with |
Principal Attribute |
| User | If a Principal type is non-blank, this field specifies the name ("Attribute [Name]") or the friendly name ("Attribute [Friendly Name]") of the identifying attribute. |
Allow create |
| User | Allow the external identity provider to create a new identifier to represent the principal. |
HTTP-POST Binding Response |
| Antavo/User | Controls the SAML binding in response to any SAML requests sent by an external IDP. When OFF, Keycloak uses Redirect Binding. |
HTTP-POST Binding for AuthnRequest |
| Antavo/User | Controls the SAML binding when requesting authentication from an external IDP. When OFF, Keycloak uses Redirect Binding. |
Want AuthnRequests Signed |
| Antavo | When ON, Keycloak uses the realm’s keypair to sign requests sent to the external SAML IDP. |
Signature Algorithm |
| User | If Want AuthnRequests Signed is ON, the signature algorithm to use. |
SAML Signature Key Name |
| Antavo | Signed SAML documents sent using POST binding contain the identification of signing key in |
Force Authentication |
| Antavo | The user must enter their credentials at the external IDP even when the user is already logged in. |
Validate Signature |
| Antavo | When ON, the realm expects SAML requests and responses from the external IDP to be digitally signed. |
Validating X509 Certificate |
| Antavo | The public certificate Keycloak uses to validate the signatures of SAML requests and responses from the external IDP. |
Sign Service Provider Metadata |
| Antavo/User | When ON, Keycloak uses the realm’s key pair to sign the SAML Service Provider Metadata descriptor. |
Pass subject |
| User | Controls if Keycloak forwards a |
Attribute Consuming Service Index |
| User | Identifies the attribute set to request to the remote IDP. Keycloak automatically adds the attributes mapped in the identity provider configuration to the autogenerated SP metadata document. |
Attribute Consuming Service Name |
| User | A descriptive name for the set of attributes that are advertised in the autogenerated SP metadata document. |
SAML 2.0 metadata configuration
The following XML example represents the metadata for a SAML 2.0 system entity serving as a service provider. This XML file can be exported from the IdP side, and the data contained within need to be transmitted to Antavo to import it to Keycloak’s server.
<EntityDescriptor
xmlns="urn:oasis:names:tc:SAML:2.0:metadata"
entityID="loadbalancer-3.example.com">
<IDPSSODescriptor
WantAuthnRequestsSigned="false"
protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<KeyDescriptor use="signing">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>
MIICZDCCAg6gAwIBAgICBr8wDQYJKoZIhvcNAQEEBQAwgZIxCzAJBgNVBAYTAlVTMRMwEQYDVQQI
EwpDYWxpZm9ybmlhMRQwEgYDVQQHEwtTYW50YSBDbGFyYTEeMBwGA1UEChMVU3VuIE1pY3Jvc3lz
dGVtcyBJbmMuMRowGAYDVQQLExFJZGVudGl0eSBTZXJ2aWNlczEcMBoGA1UEAxMTQ2VydGlmaWNh
dGUgTWFuYWdlcjAeFw0wNzAzMDcyMTUwMDVaFw0xMDEyMDEyMTUwMDVaMDsxFDASBgNVBAoTC2V4
YW1wbGUuY29tMSMwIQYDVQQDExpMb2FkQmFsYW5jZXItMy5leGFtcGxlLmNvbTCBnzANBgkqhkiG
9w0BAQEFAAOBjQAwgYkCgYEAlOhN9HddLMpE3kCjkPSOFpCkDxTNuhMhcgBkYmSEF/iJcQsLX/ga
pO+W1SIpwqfsjzR5ZvEdtc/8hGumRHqcX3r6XrU0dESM6MW5AbNNJsBnwIV6xZ5QozB4wL4zREhw
zwwYejDVQ/x+8NRESI3ym17tDLEuAKyQBueubgjfic0CAwEAAaNgMF4wEQYJYIZIAYb4QgEBBAQD
AgZAMA4GA1UdDwEB/wQEAwIE8DAfBgNVHSMEGDAWgBQ7oCE35Uwn7FsjS01w5e3DA1CrrjAYBgNV
HREEETAPgQ1tYWxsYUBzdW4uY29tMA0GCSqGSIb3DQEBBAUAA0EAGhJhep7X2hqWJWQoXFcdU7eQ
</KeyDescriptor>
<KeyDescriptor use="encryption">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
EwpDYWxpZm9ybmlhMRQwEgYDVQQHEwtTYW50YSBDbGFyYTEeMBwGA1UEChMVU3VuIE1pY3Jvc3lz
dGVtcyBJbmMuMRowGAYDVQQLExFJZGVudGl0eSBTZXJ2aWNlczEcMBoGA1UEAxMTQ2VydGlmaWNh
dGUgTWFuYWdlcjAeFw0wNzAzMDcyMjAxMTVaFw0xMDEyMDEyMjAxMTVaMDsxFDASBgNVBAoTC2V4
YW1wbGUuY29tMSMwIQYDVQQDExpMb2FkQmFsYW5jZXItMy5leGFtcGxlLmNvbTCBnzANBgkqhkiG
HREEETAPgQ1tYWxsYUBzdW4uY29tMA0GCSqGSIb3DQEBBAUAA0EAEgbmnOz2Rvpj9bludb9lEeVa
OA46zRiyt4BPlbgIaFyG6P7GWSddMi/14EimQjjDbr4ZfvlEdPJmimHExZY3KQ==
</KeyInfo>
</EncryptionMethod>
</KeyDescriptor>
<ArtifactResolutionService
index="0"
isDefault="1"/>
<SingleLogoutService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect"
<SingleLogoutService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP"
<ManageNameIDService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect"
ResponseLocation="https://LoadBalancer-3.example.com:9443/
amserver/IDPMniRedirect/metaAlias/idp"/>
<ManageNameIDService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP"
Location="https://LoadBalancer-3.example.com:9443/amserver/
IDPMniSoap/metaAlias/idp"/>
<NameIDFormat>
urn:oasis:names:tc:SAML:2.0:nameid-format:persistent
</NameIDFormat>
<NameIDFormat>
urn:oasis:names:tc:SAML:2.0:nameid-format:transient
</NameIDFormat>
<SingleSignOnService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect"
Location="https://LoadBalancer-3.example.com:9443/amserver/
SSORedirect/metaAlias/idp"/>
<SingleSignOnService
Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP"
Location="https://LoadBalancer-3.example.com:9443/amserver/
SSOSoap/metaAlias/idp"/>
</IDPSSODescriptor>
</EntityDescriptor>SAML 2’s metadata specification’s Chapter 2 offers details on the nature of this metadata.
Configuring the SSO module
The next step is to establish the connection between the Antavo and the Keycloak server by configuring the SSO module in the Management UI. To access the configuration page of the SSO module, navigate to the Modules menu and search for the SSO module in the list.
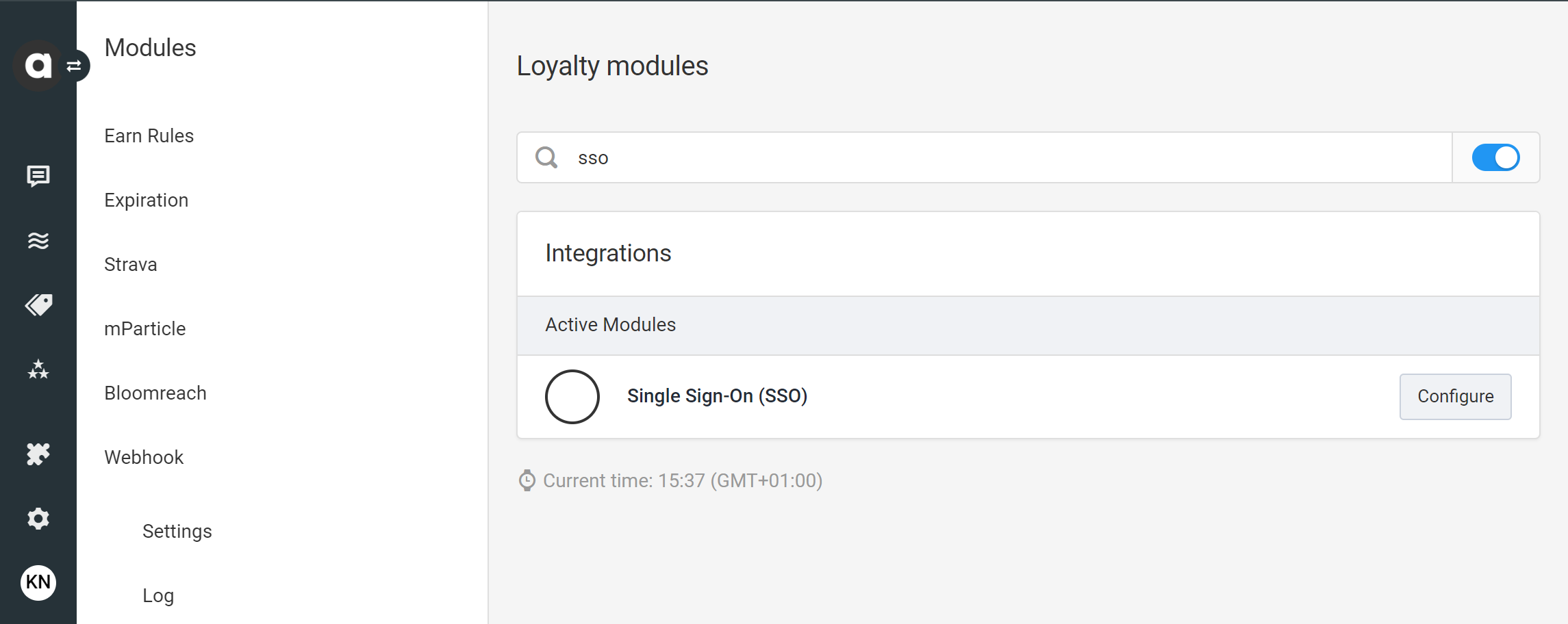
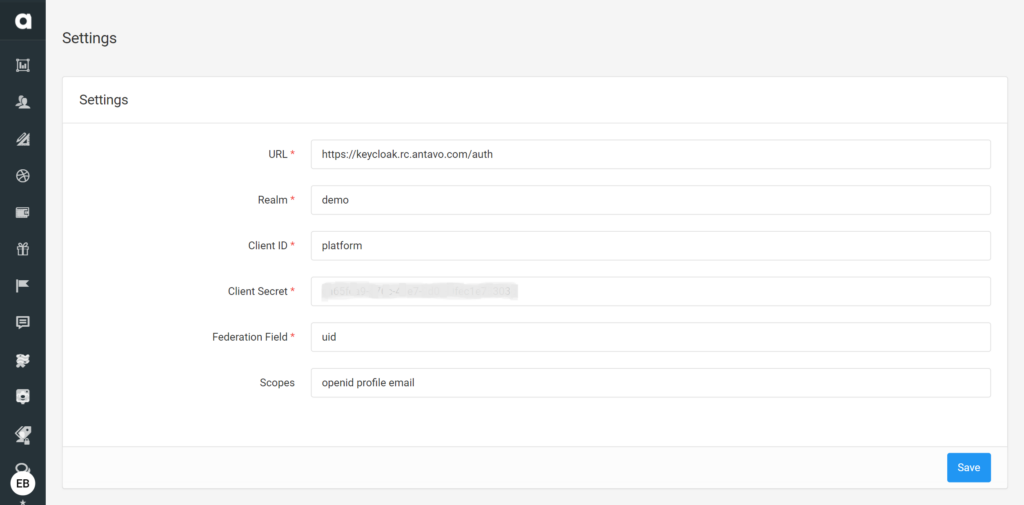
The page provides an interface to set up the connection with the following fields:
URL
Realm
User ID
User secret (generated during the Keycloak configuration)
Federation field (default value is uid)
Scopes
Please contact the Antavo Service Desk before you start configuring the module or want to make changes in the settings.
Setting up SSO login for Management UI users
The SSO Source and SSO ID of Management UI users have to be added on the user editor interface to enable SSO login. Please note that SSO login is enforced for all users by default, allowing them to log in to the Management UI through SSO. You can turn off this restriction if needed.